Remcos RAT is a powerful remote access tool that can do a number of powerful things, like record audio and video, steal digital currency, download extra payloads, and get sensitive data. Remcos is an advanced Remote Control tool that can be used to fully manage one or more computers from a distance.
You may control your computer system remotely from anywhere in the globe by using a piece of software called Remcos Professional Remote Administration Tool. This programme is both comprehensive and strong in its remote control capabilities. In addition to that, it may also be used to fully administer one or several other personal computers.
About REMCOS RAT
Remcos is a fully functional RAT that grants the threat actor complete access to the infected system and allows for the collection of data such as audio, video, screenshots, and system information. Remcos is able to install and run whatever programme it wants on the system since it has administrative privileges.
The comprehensive nature of this monitoring tool means it serves as your one and only option. Use it to keep an eye on your network from afar.
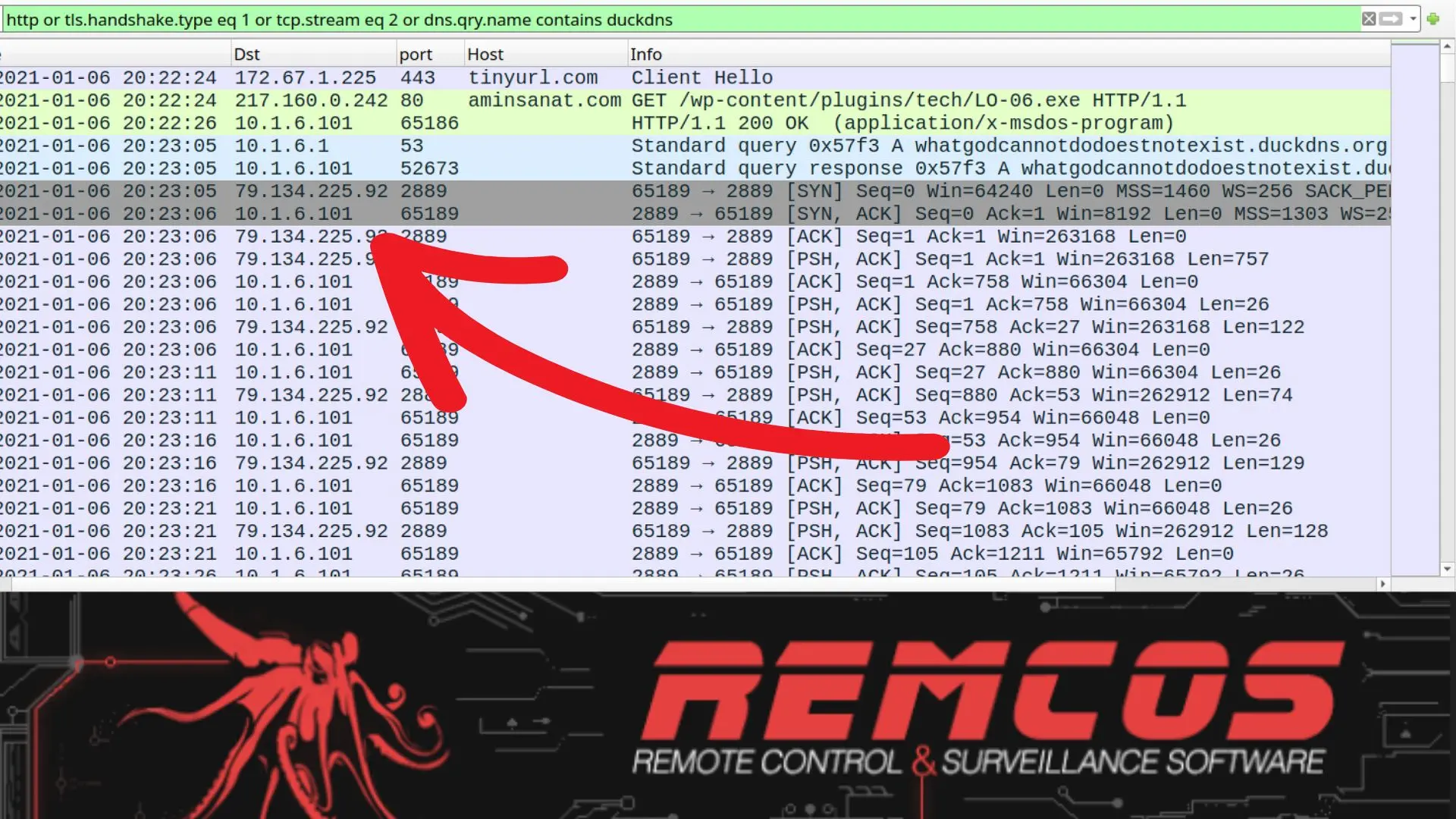
Each compromised file has a hidden macro that, when executed, launches a shell command that downloads and executes the malware. The string is obscured by simply appending junk characters to it.
You can easily find the remcos rat free download section in this article, So read the article till the end and share it with your friend.
Features of Remcos RAT
- Robust Connection
- Multi-thread
- File Manager
- Multiple Binary Payload
- Works on every window.
- Connection With Security
- Low Impact, High Performance
- Anti-theft from afar
- Proxy from afar
- File Search
- Remote Support
- Quick and simple
- Controller Surveillance
- Audits of security
Details of Remcos RAT Features:
Lates know more about Remcos RAT features one by one. So, you got a clear idea about Ramcos RAT Features:
Robust Connection
It is part of the KeepAlive system, which is used to back up connection addresses and make sure that a user’s connection to a remote host will never be lost.
Multi-thread
Users may now control one or more of their devices concurrently, and all of the features can be controlled simultaneously as well.
File Manager
Users may now explore both directories and files, upload or download files, delete or remove files, and perform many more file-related actions, among many other features.
Multiple Binary Payload
Remcos only has the UPX and MPRESS1 packers for its server component to compress and hide it. In this sample, the attacker went further by adding another layer of custom packer on top of MPRESS.
The malware was almost impossible to figure out after the two packers. As you can see in the screenshots below, the strings from the unpacked binary show that it is the server component built from the latest Remcos v2 Pro. Their website, Breaking-Security.Net, says that this version was just made public.
Works on every window.
It works with 32-bit and 64-bit versions of Windows XP through 10, as well as the server editions. For this, you don’t need the.net framework or any other extra dependencies.
Connection With Security
It comes with a custom TCP-based protocol that gives you a connection that is 100% encrypted. Not even a single byte is sent without being encrypted.
Low Impact, High Performance
It was made with performance, speed, and lightness as its top development goals. It is written well in the programming languages C++ and Delphi, which are used to make high-performance code that runs on the computer’s own hardware. It works quickly and doesn’t take up much space on your disc, memory, or processor. This makes it possible to control different machines from anywhere in the world.
Anti-theft from afar
Have you misplaced your laptop? You can now use Remcos to locate your computer, snap screenshots from the webcam, swiftly restore files to a secure location, and protect information from falling into the wrong hands by remotely erasing cookies, important data, and passwords.
Proxy from afar
Using the SOCKS5 protocol, users may utilise this as a dependable proxy. Users may now route their Internet traffic via a remote workstation, allowing them to circumvent Internet filtering, limitations, and blockages. It is also used to support both direct and reverse SOCKS5 modes.
File Search
If you prefer to search for a file on any of your selected computers, you may do a simultaneous file search on a single host, many hosts, or the whole network.
Remote Support
It is used to do remote assistance sessions with ease, due to its remote desktop and chat capabilities. Some people find remcos rat free download because it supports remote access for free.
Quick and simple
Permits proficient C++ and Delphi programming to produce high-performance programmes. It includes a 100kb agent size.
Controller Surveillance
This is a robust solution for remotely monitoring your company, terminals, and home. It also alerts you when someone gets illegal access to your computer system or conducts undesired activities on it. Additionally, it may be utilised for monitoring the surrounding room and environment.
The greatest aspect is that you just need to use one of your PCs and do not need to purchase cameras or microphones.
Audits of security
It is a trustworthy instrument for use in remote access security checks and penetration testing.
Recommended For You:
Cypher RAT V5 Full Version (Android RAT 2022) Lifetime – FREE Download
What is DNS Spoofing & Link Redirection – Safe from It in 2022
[Working] Anubis 7.0 – Unlocked Version 2022 August Updated Download
Why Use Remcos RAT
To encrypt and decode network communication between its client and server, Remcos utilises a basic RC4 technique with the password as the key. Configures the installation path, autorun registries, and a watchdog module that prohibits process termination and destruction of files and registries.
This part also has the option of having its own UAC bypass, which we hypothesized existed previously in this article. Therefore, it is conceivable that the attacker just utilised the document macro as a template to download and run the binary, and never meant to employ the script’s UAC bypass, given the server binary already had the same functionality.
In reality, it employs the same UAC bypass approach, although with an additional code to undo the changed registry after acquiring privileges. This is understandable since failure to restore the registry might result in system failures that may lead the user to be suspicious whenever an a.msc file must be accessed.
System Requirements for Remcos RAT
- Operating System: Windows XP/Vista/7/8/8.1/10/11
- RAM: 1G
- Hard Disk: 100 MB
- Processor: Intel Dual Core or higher processor
REMCOS RAT Setup File Details
- Software Full Name: Remcos RAT Latest Lifetime 2022
- Setup File Name: Remcos RAT_lifetime.rar
- Setup Size: 12 MB
- Compatibility : 32 Bit (x86) / 64 Bit (x64)
REMCOS RAT Free Download 2022
Just click the link and get the remcos rat free download. you can use 32bit and also 64bit Operating systems.
FAQs About Remcos RAT
Q.1. Why Need Remcos RAT?
Remcos RAT lets people connect to the system they need even when they can’t be there in person. To put it another way, users can access the systems from a distance using telecommunications or the internet. Remote Access Services is a good way for companies to connect their own networks to the system and each other.
Q.2. Can you remote access a computer when it’s off?
With Remcos Rat software, it’s easy to set up and use, and you can connect to your remote computer from anywhere, even if it’s turned off, in hibernation mode (on Windows).
Q.3. How do I access a remote IP address with Remcos RAT?
When it comes to hosted and Internet-accessible VPS servers, things are a lot different than they were a few years ago because servers can now be thousands of miles away. Microsoft has a feature called “Remote Desktop” that lets you access the desktop of a Windows server that is hosted on the Internet.